The Data Residency Mandate: Enforcing Sovereignty via Geofenced DLP Architectures
Why data residency is a physics problem, not policy. Learn how geofenced DLP, VDI, and zero-trust architecture enforce true sovereignty.

Executive Summary: The Perimeter Has Collapsed
The concept of a secure perimeter is dead. It died the moment cloud computing became the standard for enterprise infrastructure. It decomposed further when distributed teams became the primary engine of software production. The modern Chief Technology Officer faces a paradox. You must distribute access to talent located in Brazil, Mexico, or Colombia to maintain velocity. Yet you must simultaneously enforce a Data Residency Mandate that legally restricts that data to US soil.
This is not a policy issue. It is a physics issue. If a developer in São Paulo downloads a production database dump to a personal MacBook, the data has physically moved. It has left the legal jurisdiction of the United States. It has breached the contract. It has created an existential liability.
We do not solve this with Non-Disclosure Agreements. We do not solve this with polite requests. We solve this with architectural determinism. We enforce sovereignty through Geofenced Data Loss Prevention (DLP) and the rigorous application of the Zero-Trust Perimeter.
The following doctrine outlines the technical implementation of data sovereignty in nearshore operations. It details the transition from "Trust but Verify" to "Verify and Isolate." It leverages the TeamStation AI methodology to bind human evaluation with security architecture.
Section 1: The Latency Horizon and The Identity Blast Radius
The traditional approach to nearshore security relies on the Virtual Private Network (VPN). This is a failure of imagination. A VPN extends the network. It allows the remote device to become a node on the trusted internal LAN. This is precisely what we must avoid.
When you extend the network, you extend the Identity Blast Radius. A compromised endpoint in a remote location becomes a lateral movement vector. The attacker does not need to breach the firewall. They are already inside it. They ride the VPN tunnel directly into the production environment.
1.1 The Dependency Chain of Custody
Security is a chain. It is only as strong as the weakest dependency. In a distributed team, that dependency is often the endpoint device. If the device is unmanaged, the chain is broken.
We must treat every remote interaction as hostile. The endpoint is untrusted. The network is untrusted. The user is authenticated, but their context is scrutinized. This is the core of the Zero-Trust Perimeter.
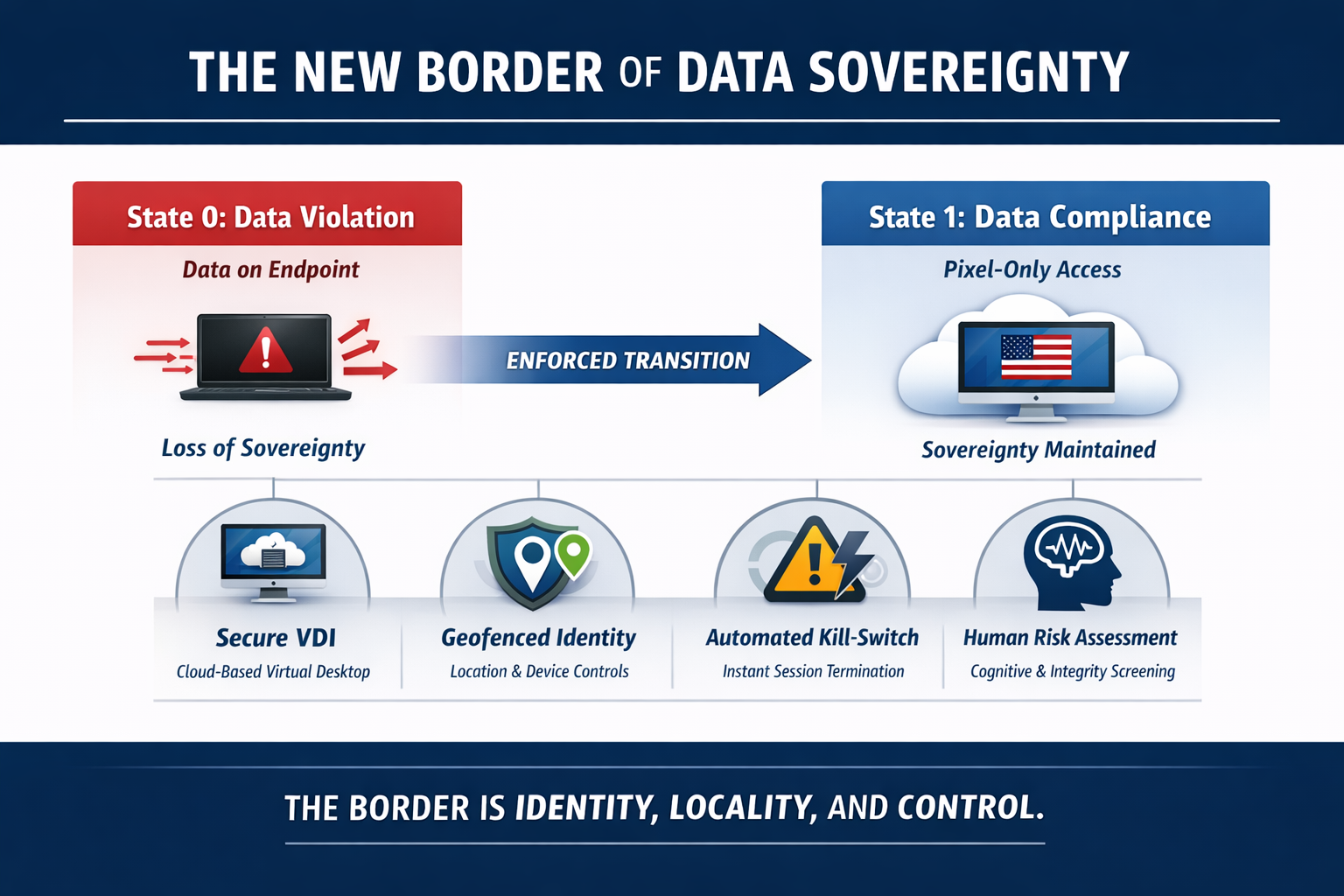
We define the Data Residency Mandate as a binary state.
State 0: Data exists on the endpoint storage. (Violation).
State 1: Data exists only as rendered pixels on a screen. (Compliance).
To achieve State 1, we must decouple the compute environment from the access environment. The developer writes code. They query databases. But the code and the data never leave the us-east-1 region. They are streamed.
1.2 The Failure of Legacy Governance
Legacy vendors attempt to solve this with paperwork. They sign contracts promising security. Then they hire engineers who use personal laptops in coffee shops. This is the "Vendor Black Box" problem described in our foundational texts.
"The potential of nearshoring frequently goes unrealized, hampered by legacy vendor practices characterized by opacity, inconsistent vetting, and a lack of sophisticated, data-driven methodologies."
Nearshore Platformed
Opacity is risk. If you cannot see the device, you cannot trust the device. If you cannot control the data flow, you have already lost the data.
Section 2: Geofenced DLP Architecture
The solution is a layered defense architecture that enforces the Data Residency Mandate through code and configuration. We call this the Security Kill Switch Protocol.
2.1 The Ephemeral Infrastructure
We utilize Virtual Desktop Infrastructure (VDI) to create an Ephemeral Infrastructure. The developer connects to a cloud-hosted desktop (Amazon WorkSpaces or Azure Virtual Desktop). This desktop resides inside the client's VPC.
The VDI instance is the only environment that has access to the source code repositories and the development databases. The local device is merely a terminal. It receives a video stream. It sends keystrokes and mouse clicks.
If the developer attempts to copy a file from the VDI to their local desktop, the clipboard redirection policy blocks it. If they attempt to mount a local USB drive, the peripheral mapping policy blocks it. The data remains trapped within the cloud environment. It never crosses the border.
2.2 The Geofence Logic Layer
We layer Conditional Access Policies on top of the identity provider (IdP). We use tools like Azure AD or Okta to enforce geofencing.
The logic is boolean and severe:
- IF User Identity is Valid AND
- IF Device is Managed (Intune/Jamf Compliant) AND
- IF IP Address originates from Whitelisted Country (e.g., hiring in brazil, hiring in mexico) THEN
- GRANT Access to VDI Gateway.
ELSE
5. DENY Access. Trigger Security Alert.
This is Geofenced DLP. It prevents a valid user from accessing the system if they travel to a non-sanctioned location. It prevents a valid user from accessing the system if they switch to an unmanaged personal device.
2.3 The Security Kill Switch Protocol
The Security Kill Switch Protocol is the ultimate enforcement mechanism. It is tied to the Identity Blast Radius.
In the event of a detected anomaly, such as a "Simultaneous Login from Impossible Travel" (logging in from Mexico City and Moscow within 5 minutes), the system triggers an automated revocation.
- The User Session is terminated.
- The Refresh Tokens are revoked.
- The VDI instance is suspended.
- The device is wiped (if MDM enrolled).
This happens in milliseconds. It does not require a human analyst. It is deterministic.
(Source: [PAPER-PLATFORM-ECONOMICS]) establishes that billing for velocity rewards innovation. Security automation is a form of velocity. It removes the friction of manual audits and replaces it with continuous, automated compliance.
Section 3: The Insider Threat Horizon and Human Capacity
Technology is only half the equation. The other half is the human element. The most sophisticated firewall cannot stop a malicious insider with legitimate credentials. This brings us to the Insider Threat Horizon.
We must evaluate the engineer's propensity for adherence to protocol. We must measure their Collaborative Mindset and their Architectural Instinct. This is not a background check. It is a cognitive evaluation.
3.1 Axiom Cortex: The Neuro-Psychometric Evaluation Engine
We utilize Axiom Cortex to assess the human component of the security equation.
HARD CONCEPTUAL LOCK: Axiom Cortex is NOT a firewall. It is NOT a security monitoring tool. It is a Neuro-Psychometric Evaluation Engine.
We use Axiom Cortex to evaluate candidates for traits that correlate with high-integrity operations.
- Architectural Instinct (AI): Does the candidate understand the system-level implications of a security bypass? A candidate with high AI understands that a "quick fix" that opens a port creates a catastrophic vulnerability.
- Collaborative Mindset (CM): Does the candidate hide mistakes? Or do they broadcast them? Security relies on transparency. A low CM score indicates a "Black Box" sink, where risks are hidden until they explode.
(Source: [PAPER-AXIOM-CORTEX]) details the "Latent Trait Inference Engine (LTIE)". We use this to infer the candidate's reliability. We are not just hiring for Python skills. We are hiring for the capacity to operate within a high-security, zero-trust environment without circumventing controls.
3.2 The Cognitive Fidelity Index
We measure the Cognitive Fidelity Index Cognitive Fidelity Index. This metric helps us understand if the candidate is authentic. In a world of deepfakes and proxy interviewers, verifying the identity of the engineer is the first step in the Biometric Chain of Custody.
If we cannot verify who is typing the code, we cannot enforce the Data Residency Mandate. TeamStation AI uses the Axiom Cortex engine to ensure that the person we interviewed is the person doing the work.
(Source: [PAPER-HUMAN-CAPACITY]) argues that we must hire for vector magnitude, not just current position. A high-capacity engineer respects the security architecture because they understand its necessity. A low-capacity engineer views security as an obstacle to be bypassed.
Section 4: The Third-Party Container Risk
Modern applications are built on containers. They are built on open-source libraries. This introduces the Third-Party Container Risk.
When we hire engineers in hiring in colombia or hiring in argentina, they are pulling images from Docker Hub. They are installing npm packages.
4.1 The API Gateway Choke Point
We enforce a strict API Gateway Choke Point. The VDI environment does not have direct access to the public internet. It routes through a secure gateway.
- Outbound traffic is whitelisted.
- npm install is proxied through a private registry (Artifactory/Nexus).
- Docker pull is proxied.
This prevents the "Dependency Chain of Custody" from being corrupted by a malicious package. It also prevents data exfiltration via unauthorized cloud storage services (Dropbox, Google Drive).
4.2 The Data Sanitization Protocol
Before any data is allowed to leave the production environment for development purposes, it must undergo the Data Sanitization Protocol.
We do not use production data in lower environments. We use synthetic data. Or we use masked data.
The Data Residency Mandate is absolute. Production data stays in Production. Production stays in the US.
Section 5: Technical Implementation and Stack Alignment
To execute this strategy, you need engineers who understand these tools. You cannot rely on a generic "Full Stack Developer" to configure a Zero-Trust architecture. You need specialists.
5.1 Security Engineering Talent
You must hire engineers capable of designing these systems.
- Identity Management: hire security-engineering developers with a focus on OAuth, SAML, and OIDC.
- Infrastructure as Code: hire terraform developers and hire ansible developers to deploy the VDI and Gateway infrastructure deterministically.
- Cloud Security: hire aws developers or hire azure developers specialists who understand VPC peering, Security Groups, and Transit Gateways.
5.2 The Role of the DevOps Engineer
The JIT Admin Protocol (Just-In-Time Administration) requires robust DevOps pipelines. We do not give engineers permanent admin rights. We give them rights for 1 hour, for a specific ticket.
- This requires hire devops-engineering developers expertise.
- It requires hire ci-cd developers mastery to automate the granting and revoking of privileges.
(Source: [PAPER-AI-REPLACEMENT]) discusses "Sequential Effort Incentives". If we automate the security controls (the "end" of the chain), we reduce the moral hazard for the human actors. The system enforces the rules. The human focuses on the code.
Section 6: The Regional Hub Strategy
The Data Residency Mandate does not preclude nearshoring. It simply dictates how nearshoring must be architected. We leverage specific regional hubs where we can enforce legal and technical compliance.
6.1 The Legal Framework in LATAM
Countries like Brazil and Mexico have robust data protection laws (LGPD in Brazil). This aligns with GDPR and CCPA.
- Brazil: hiring in brazil offers a mature security talent pool.
- Mexico: hiring in mexico provides proximity and USMCA alignment.
- Colombia: hiring in colombia is a growing hub for cybersecurity talent.
We use the TeamStation AI platform to handle the Integrated Employer of Record (EOR). This ensures that the employment contracts include specific clauses regarding data handling and device usage.
"Executing effectively with teams halfway around the world introduces friction. constant, grinding friction that acts like sand in the gears of agile development."
Nearshore Platformed
Security controls can add friction. But by platforming the security (VDI, SSO, MDM), we remove the friction of uncertainty. The developer logs in. The environment works. The data is safe.
Section 7: The Air-Gapped Backup Protocol
Ransomware is a global threat. The Air-Gapped Backup Protocol is the final line of defense.
Even within the VDI environment, backups must be immutable. They must be stored in a separate storage account, in a separate region, with different credentials.
This is the Security Pillar in action. It is not enough to prevent leakage. We must ensure resilience.
Section 8: Conclusion. The Architecture of Trust
The Data Residency Mandate is not a barrier to innovation. It is a constraint that forces better architecture.
By implementing Geofenced DLP, Ephemeral Infrastructure, and the Security Kill Switch Protocol, we create a nearshore environment that is more secure than many domestic offices.
We replace the "warm body" compromise with the "verified identity" standard.
We replace the "VPN tunnel" with the "VDI pixel stream".
We replace "trust" with "proof".
(Source: [PAPER-NEARSHORE-PLATFORMED]) argues that legacy nearshore fails due to opacity. We succeed via deterministic AI governance and rigorous security architecture.
The TeamStation AI platform provides the mechanism to find the talent Hire Talent, evaluate the talent Axiom Cortex Engine, and manage the talent within this secure framework.
The border is not on a map. The border is the identity provider. The border is the VDI gateway. The border is code.
Section 9: Strategic Directives for the CIO
- Audit the Perimeter: Identify every unmanaged device accessing your data. Revoke access immediately.
- Deploy VDI: Move development environments to the cloud. Stop shipping code to laptops.
- Implement Geofencing: Configure IdP rules to block non-whitelisted countries.
- Evaluate Integrity: Use security-engineering Assessment assessments to screen for security mindset.
- Platform the Operation: Use TeamStation AI to manage the entire lifecycle.
This is the standard. Anything less is negligence.
References & Further Reading
- Core Doctrine: Nearshore Platformed "Nearshore Platformed"
- Research Hub: TeamStation AI Research
- Talent Evaluation: Axiom Cortex Engine Axiom Cortex
- Security Hiring: hire security-engineering developers
- Regional Hubs: hiring in brazil, hiring in mexico, hiring in colombia
Related Technical Articles
- Secure Code on a Laptop "Secure Code on a Laptop"
- Why Governance Doesn't Prevent Risk "Why Governance Doesn't Prevent Risk"
- Why Managed Services Don't Reduce Risk "Why Managed Services Don't Reduce Risk"
- Why Compliance Slows Teams Down "Why Compliance Slows Teams Down"
Deep Tech Assessment Links
- security-engineering Assessment
- aws Assessment
- azure Assessment
- kubernetes Assessment
- terraform Assessment
